19+ Biometric Access Control System Pdf
An alternative of access control in the strict sense physically controlling access itself is a system of checking authorized presence see eg. There are three systems which are referred to using the NHS name NHS England NHS Scotland and NHS WalesHealth and Social Care in Northern Ireland was created separately.

Pdf Fingerprint Biometric System Hygiene And The Risk Of Covid 19 Transmission
The PAG Physical Access Group is a special branch within the CCI Center for Cyber Intelligence.
. The National Health Service NHS is the umbrella term for the publicly funded healthcare systems of the United Kingdom UK. The ability to prove ones identity is an essential precursor for social political and economic empowerment. A role a system might perform by mediating the creation and verification of identifiers keys and other relevant data such as verifiable credential schemas revocation registries issuer public keys and so on which might be required to use verifiable credentials.
With advanced alarm and identity management ACM provides superior control of access to facilities. Department of State duplicate copies are. It works perfectly for any document conversion like Microsoft Word Excel PowerPoint PDF Google Docs Sheets and many more.
News and opinion from The Times The Sunday Times. The differences between a data warehouse vs. A method is provided for acquiring and transmitting biometric data eg vital signs of a user where the data is analyzed to determine whether the user is suffering from a viral infection such as COVID-19.
These Revised 508 Standards which consist of 508 Chapters 1 and 2 Appendix A along with Chapters 3 through 7 Appendix C contain scoping and technical requirements for information and communication technology ICT to ensure accessibility and usability by individuals with disabilities. Application and Administration E101 General E1011 Purpose. Links with this icon indicate that you are leaving the CDC website.
Patent Public Search has two user selectable modern interfaces that provide enhanced access to prior art. This can include observation from a distance by means of electronic equipment such as closed-circuit television CCTV or interception of electronically transmitted information like Internet traffic. Surveillance is the monitoring of behavior many activities or information for the purpose of information gathering influencing managing or directing.
Border guard bouncer ticket checker or with a device such as a turnstileThere may be fences to avoid circumventing this access control. Border security crime investigations background checks and access control all rely on certain organizations being able to seamlessly exchange biometric data Software Usability Companies in every industry need software that their employees and customers can easily learn to use without error but for years there was no way for them to. Due to enhanced electronic scanning capabilities and data-sharing with the US.
Data marts and data warehouses both play key roles in the BI and analytics process. Geographical access control may be enforced by personnel eg. A method is provided for acquiring and transmitting biometric data eg vital signs of a user where the data is analyzed to determine whether the user is suffering from a viral infection such as COVID-19.
11 2022 we no longer require petitioners to submit a duplicate copy of Form I-129 Petition for a Nonimmigrant Worker or a duplicate copy of any of the supporting documentation unless we specifically ask you to do so. Since 1948 they have been funded out of general taxation. Biometric authentication or realistic authentication is used in computer science as a form of identification and access control.
The method includes using a pulse oximeter to acquire at least pulse and blood oxygen saturation percentage which is transmitted wirelessly to a smartphone. Administration control superior patient care strict cost control and improved profitability. Its task is to gain and exploit physical access to target computers in CIA field operations.
Compose the content. Biometric identifiers are the distinctive measurable characteristics used to label and describe. The biometric de-duplication system is designed to identify as duplicate those cases where any one of the biometrics ten fingers and two irises match.
A biometric passport also known as an e-passport or a digital passport is a traditional passport that has an embedded electronic microprocessor chip which contains biometric information that can be used to authenticate the identity of the passport holder. The Patent Public Search tool is a new web-based patent search application that will replace internal legacy search tools PubEast and PubWest and external legacy search tools PatFT and AppFT. The nuclear program of Iran is an ongoing scientific effort by Iran to research nuclear technology that can be used to make nuclear weaponsIran has several research sites two uranium mines a research reactor and uranium processing facilities that include three known uranium enrichment plants.
Word HTML is the perfect tool to edit the source code of WordPress articles or any other content management system when their built in composer doesnt provide all functionalities we need. But most current ID systems are archaic insecure lack adequate privacy protection and for nearly a billion people globally entirely inaccessible. Linking to a non-federal website does not constitute an endorsement by CDC or any of its employees of the sponsors or the information and products presented on the website.
Biometrics are body measurements and calculations related to human characteristics. Irans nuclear program was launched in the 1950s with the help of the United States. We need to get digital ID right.
Dumbo can identify control and manipulate monitoring and detection systems on a target computer running the Microsoft Windows operating sytem. Visa requirements for Malaysian citizens are administrative entry restrictions by the authorities of other states placed on citizens of MalaysiaAs of 19 July 2022 Malaysian citizens had visa-free or visa on arrival access to 179 countries and territories ranking the Malaysian passport 13th in the world according to the Henley Passport Index making it the 2nd highest-ranked passport in. The method includes using a pulse oximeter to acquire at least pulse and blood oxygen saturation percentage which is transmitted wirelessly to a smartphone.
Newsroom Your destination for the latest Gartner news and announcements. HMS is powerful flexible and easy to use and is designed and developed to deliver real. It is highly improbable for the biometrics to.
It uses contactless smart card technology including a microprocessor chip computer chip and antenna for both power to. Some configurations might require correlatable identifiers for subjects. The Centers for Disease Control and Prevention CDC cannot attest to the accuracy of a non-federal website.
This 100 browser-based solution offers the flexibility to respond to alerts from anywhere. Access Control Manager ACM is a physical access control system for enterprise-class installations designed to protect people property and assets. However very often it is found that all the biometrics match.
On devices that run Android 44 API level 19 and higher your app can interact with a documents provider including external storage volumes and cloud-based storage using the Storage Access FrameworkThis framework allows users to interact with a system picker to choose a documents provider and select specific documents and other files for your app to. It is also used to identify individuals in groups that are under surveillance.

Pdf Biometric Fingerprint Implementation For Presence Checking And Room Access Control System

Pdf Design Of A Gsm Based Biometric Access Control System

Pdf Fingerprint Biometric Based Access Control And Classroom Attendance Management System
Foods Free Full Text Investigation Of Covid 19 Impact On The Food And Beverages Industry China And India Perspective
Access Control Biometric Dealers In Hyderabad Automatic Electric Gates In Hyderabad Access Control Services In Hyderabad

Pdf Biometric Access Control System Using Iot With Login Alert Message Semantic Scholar

Access Control System 100 Options Rfid Biometric Access Control

Pdf Design And Development Of A Fingerprint Door Access Control System With A Buzzer Alarm

Lenovo Thinkpad X230 Benutzerhandbuch Pdf Herunterladen Manualslib

Pdf Introduction To The Biometric Access Control Systems For Managers Which Error Indicator Matters In The Selection

Pdf Die Militarische Planung Des Deutschen Reiches Im Ersten Weltkrieg Holger Afflerbach Academia Edu

Pdf Iot Based Biometric Access Control System Semantic Scholar

Pdf Fingerprint Biometric Based Access Control And Classroom Attendance Management System

Pdf Biometric Access Control System Using Iot With Login Alert Message Semantic Scholar

Pdf Fingerprint Biometric Based Access Control And Classroom Attendance Management System
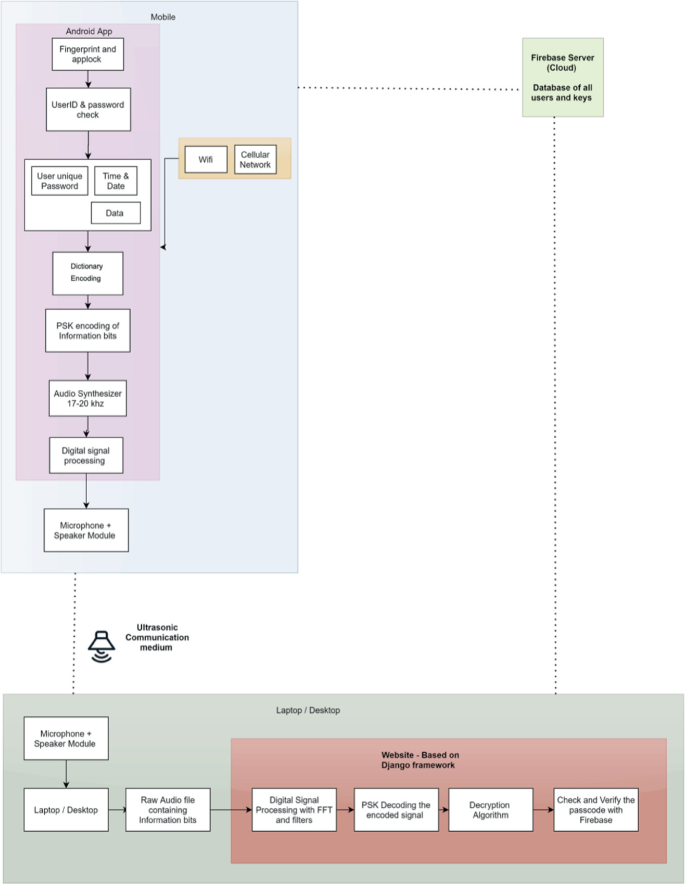
Ultrasonic Based Two Factor Authentication System For Web Applications Springerlink

40 Access Control System Ideas Access Control System Access Control Biometrics